Isolating IoT devices on Ubiquiti UniFi
These instructions/screenshots were from an UDM Pro running:
UniFi OS UDM Pro 1.11.0 UniFi Network Application 7.0.23
Why
From the FBI field office in Portland:
Your fridge and your laptop should not be on the same network.1
If those cheap "smart" lightbulbs you bought off Amazon get compromised because of an unpatched security flaw, the private information on other network devices could be at risk.
Keeping "smart" IoT devices segmented from the rest of your network is a good idea.
IoT
At some point today, you have most likely used something that would be considered an IoT.
What is IoT?
The Internet of Things (IoT) describes the network of physical objects—“things”—that are embedded with sensors, software, and other technologies for the purpose of connecting and exchanging data with other devices and systems over the internet.2
What are IoT devices?
What I consider an IoT, or "smart" device:
- Device is configured with an IP address
- Runs something other than Windows, Linux, macOS, iOS, or Android
- Caveat on Android devices, as Android seems to becoming more popular for IoT devices:
- They don't store personal data (for example a TV)
- They don't need access to any storage media (for example a Chromecast)
Use cases
You want to be able to use your mobile phone to adjust the temperature of your "smart" thermostat, but you want to prevent that thermostat from ever being able to access your mobile phone.
Desired behavior
Any device on the Trusted Network will be able to connect to any device on either the IoT.
However, devices on the IoT network can only respond to traffic sent from the Trusted Network, and can't initiate traffic to devices on the Trusted Network.
In a perfect world, we would have our network configured into micro-segments, so even devices on the Trusted Network would be further segments, such as mobile phones on one segment, Windows/Linux/macOS computers on another, etc. For the home network, this is overkill.
Create a network/SSID for the IoT devices
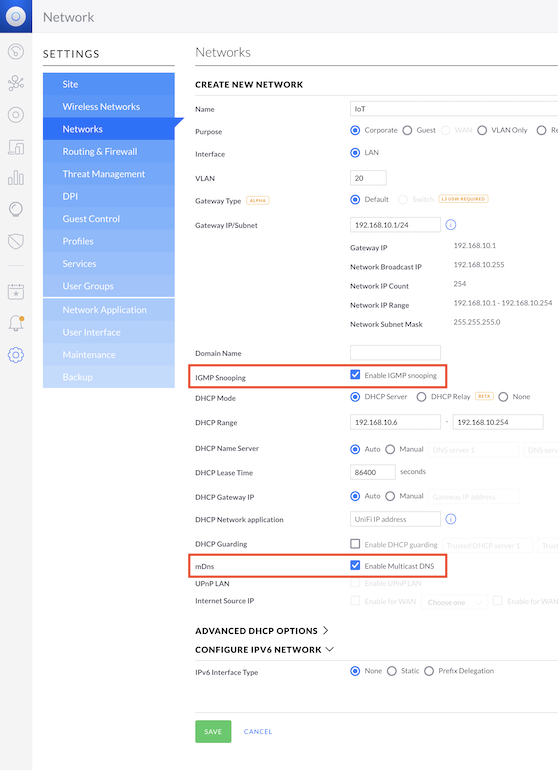
Create the IoT network
In the Classic UI:
UniFi OS --> Network --> Settings --> Networks --> + CREATE NEW NETWORK
- Name: IoT
- VLAN: 20 *
- Gateway IP/Subnet: 192.168.10.1/24 *
- Click UPDATE DHCP RANGE
- IGMP Snooping: Enable, by checking the box
- mDns: Enable, by checking the box
Create the IoT wireless network
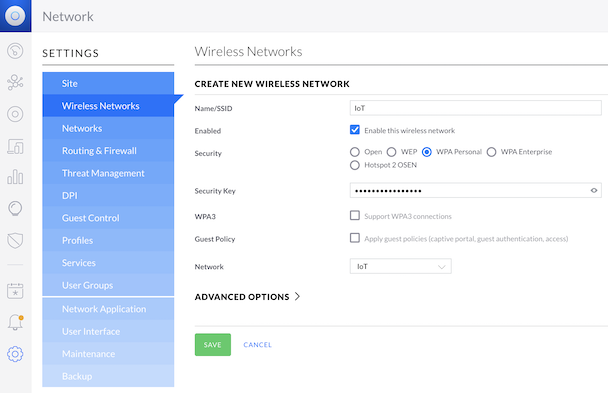
In the Classic UI:
UniFi OS --> Network --> Settings --> Wireless Networks --> + CREATE NEW NETWORK
- Name: IoT
- Security: WPA Personal
- Security Key: SomeRandomString (use something else obviously)
- Network: IoT (the one we created above)
Move IoT devices to use the new IoT wireless network
As most IoT devices are wireless, configure the IoT devices to use the new IoT SSID.
Test to make sure everything works ok, before we start locking anything down.
FYI, your Sonos speakers, Chromecast, and Apple AirPlay won't work, or work 100%...more on those in another posts. Well, except the Apple AirPlay, as I don't have/use anything that uses Apple AirPlay...
Create firewall rules to allow/block traffic
At this point, devices on the Trusted Network can communicate with devices on the IoT network, and the reverse is also true.
We need to create some firewall rules so devices on the IoT network can only reply to traffic from devices on the Trusted Network, and not initiate traffic to devices on the Trusted Network.
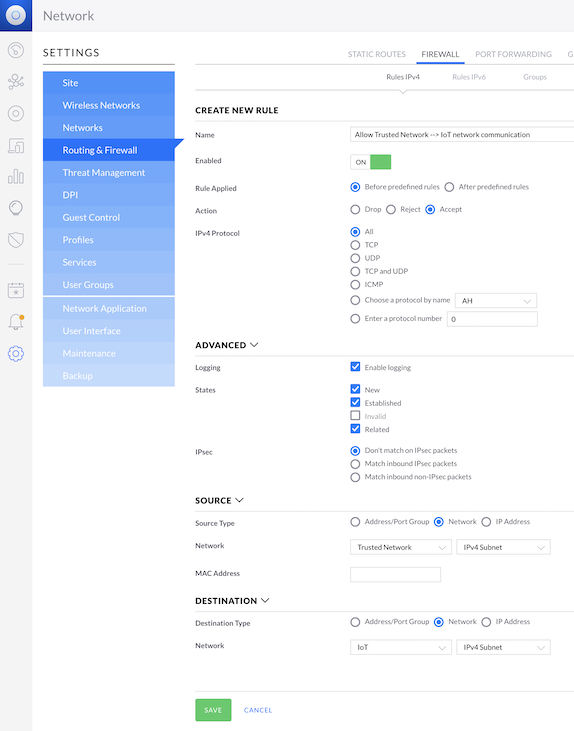
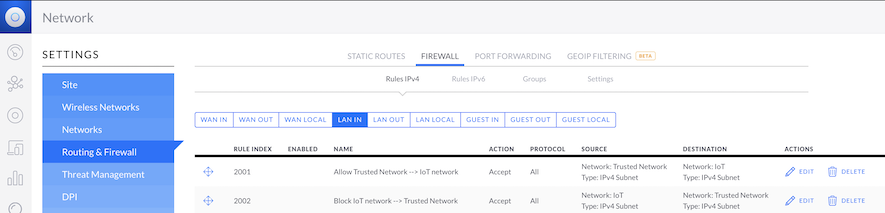
Create allow firewall rule for the Trusted Network --> IoT network
In the Classic UI:
UniFi OS --> Network --> Settings --> Routing & Firewall --> Firewall --> LAN IN --> + CREATE NEW RULE
- Name: Allow Trusted Network --> IoT network
- Rule Applied: Before predefined rules
- Action: Accept
- IPv4 Protocol: All
- Advanced
- Logging: Enable, by checking the box (turn this off later)
- States: New, Established, Invalid, Related
- Source
- Source Type: Network
- Network: Trusted Network
- Destination
- Destination Type: Network
- Network: IoT
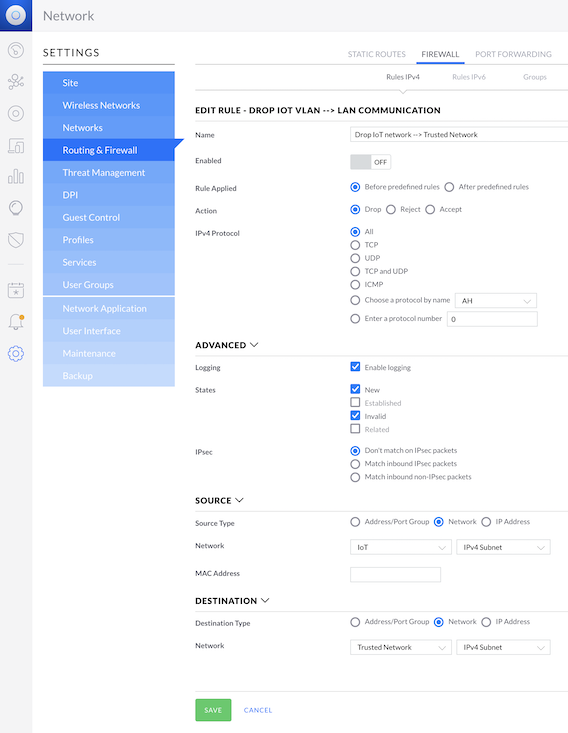
Create block firewall rules for the IoT --> Trusted Network
In the Classic UI:
UniFi OS --> Network --> Settings --> Routing & Firewall --> Firewall --> LAN IN --> + CREATE NEW RULE
- Name: Block IoT network --> Trusted Network
- Rule Applied: Before predefined rules
- Action: Drop
- IPv4 Protocol: All
- Advanced
- Logging: Enable, by checking the box
- States: New, Invalid
- Source
- Source Type: Network
- Network: IoT
- Destination
- Destination Type: Network
- Network: Trusted Network
At this point, any device on your Trusted Network can send traffic with any device on the IoT, but devices on the IoT network are prevented from initiating traffic to devices on the Trusted Network.
Just make sure the Allow firewall rule is above the Block rule:
Reference
Rob Pickering - Ubiquiti - Configure micro-segmentation for IoT devices https://robpickering.com/ubiquiti-configure-micro-segmentation-for-iot-devices/
Guide: Creating an Isolated Ubiquiti Unifi IoT Network https://vninja.net/2019/08/12/unifi-iot-networks/
-
Tech Tuesday: Internet of Things (IoT) https://www.fbi.gov/contact-us/field-offices/portland/news/press-releases/tech-tuesday-internet-of-things-iot ↩︎
-
Oracle - What is IoT? https://www.oracle.com/internet-of-things/what-is-iot/ ↩︎